Why I moved my blog to RIFE2 after 23 years?
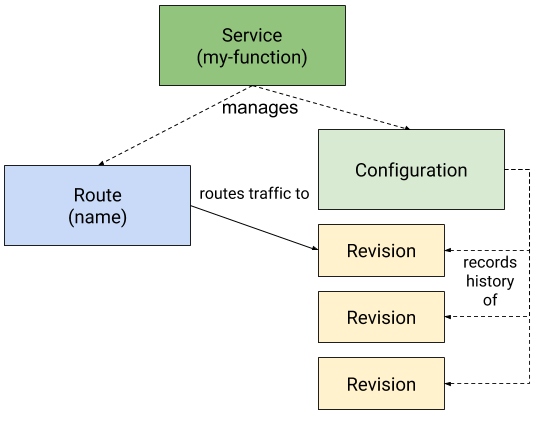
In April 2023, I decided to move my blog to RIFE2, a full-stack framework. It was previously built using my own custom JSP tag library, which ran non-stop for 23 years. At one point in time, it was handling close to 5 connections per second, or around 12 million a month, on a single Apache/Tomcat instance. Over the years, I …
Read More » NLJUG – Nederlandse Java User Group NLJUG – de Nederlandse Java User Group – is opgericht in 2003. De NLJUG verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Java Technology.
NLJUG – Nederlandse Java User Group NLJUG – de Nederlandse Java User Group – is opgericht in 2003. De NLJUG verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Java Technology.