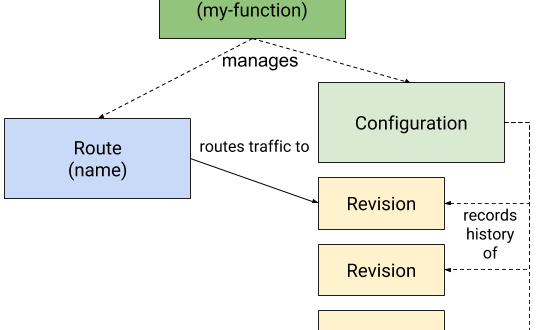
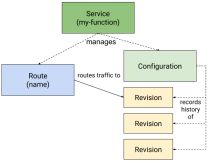
Beste leden van de NLJUG-community, Inmiddels ligt de nieuwste editie van het Java Magazine bij …
Read More »BLOG: NLJUG MASTERCLASS QUARKUS
NLJUG Academy Masterclass: Modern Development with Quarkus By Susanne Pieterse – Java developer Introduction I recently had the pleasure of attending the NLJUG academy Masterclass meetup focused on modern development with Quarkus. I’m excited to share my insights with you. First and foremost, a heartfelt shout-out to the NLJUG team and the speakers of the evening, Joran Bergfeld and Dirk …
Read More » NLJUG – Nederlandse Java User Group NLJUG – de Nederlandse Java User Group – is opgericht in 2003. De NLJUG verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Java Technology.
NLJUG – Nederlandse Java User Group NLJUG – de Nederlandse Java User Group – is opgericht in 2003. De NLJUG verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Java Technology.